API Connect Reserved Instance - configure IAM
More and more people are signing up to IBM API Connect Reserved Instance. IBM API Connect Reserved Instance allows you to have all the benefits of API Connect while IBM manages the infrastructure so you can just bring your developers and publish APIs. Also you can bring in additional Gateway Services from a different location or from your Data Center to be managed by API Connect in RI.
One of the common questions I am asked is how do we configure complex user topologies to allow only subsets of users to each role.
Thanks to Ricky Moorhouse for his help and support putting this together
In IAM you need to configure two things
- A role - collection of permissions
- Access Group - collection of users
You then apply the role to the access group and specify which RI provider org is for.
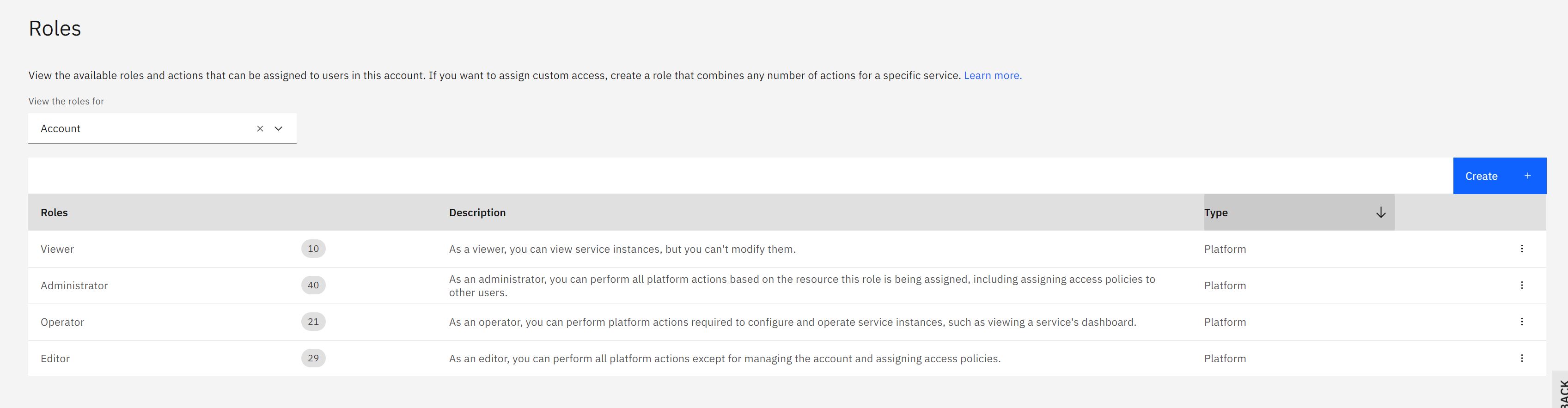
Create a role
To create a role, login into https://cloud.ibm.com/iam/roles
Click on Create
- Enter a Name, ID and Description
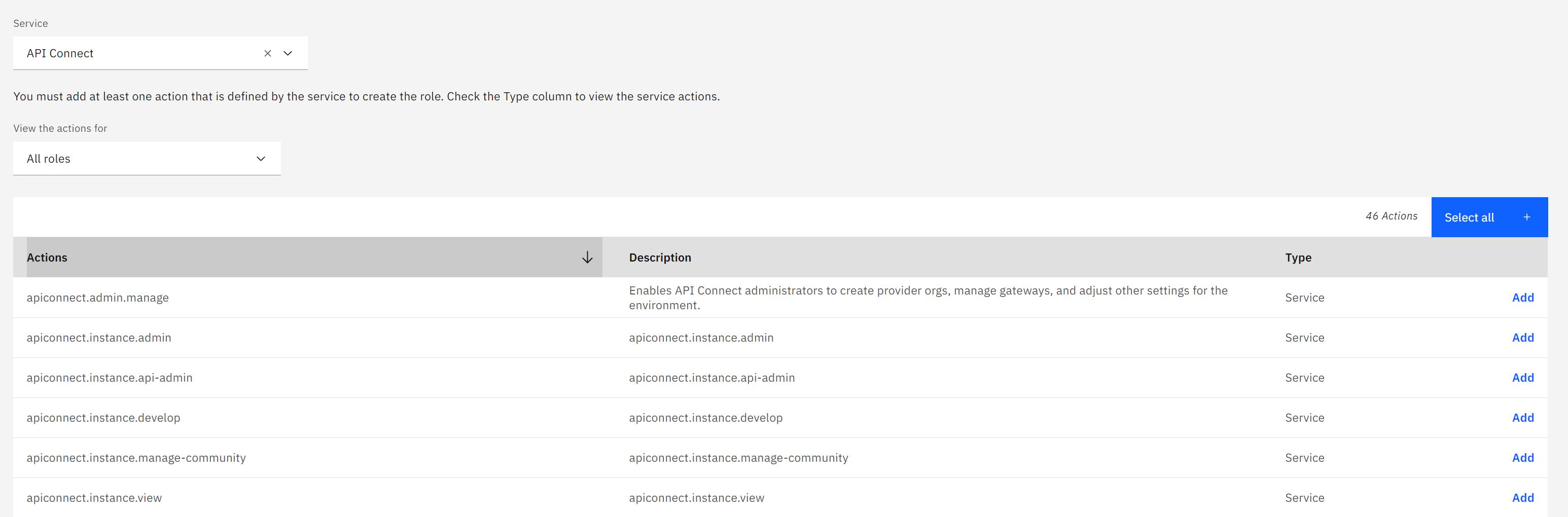
- Select
API Connectfrom the service. - Select the permissions you wish to assign to the role.
Today the only granularity we allow is the role level, not individual permissions.
Click on Create
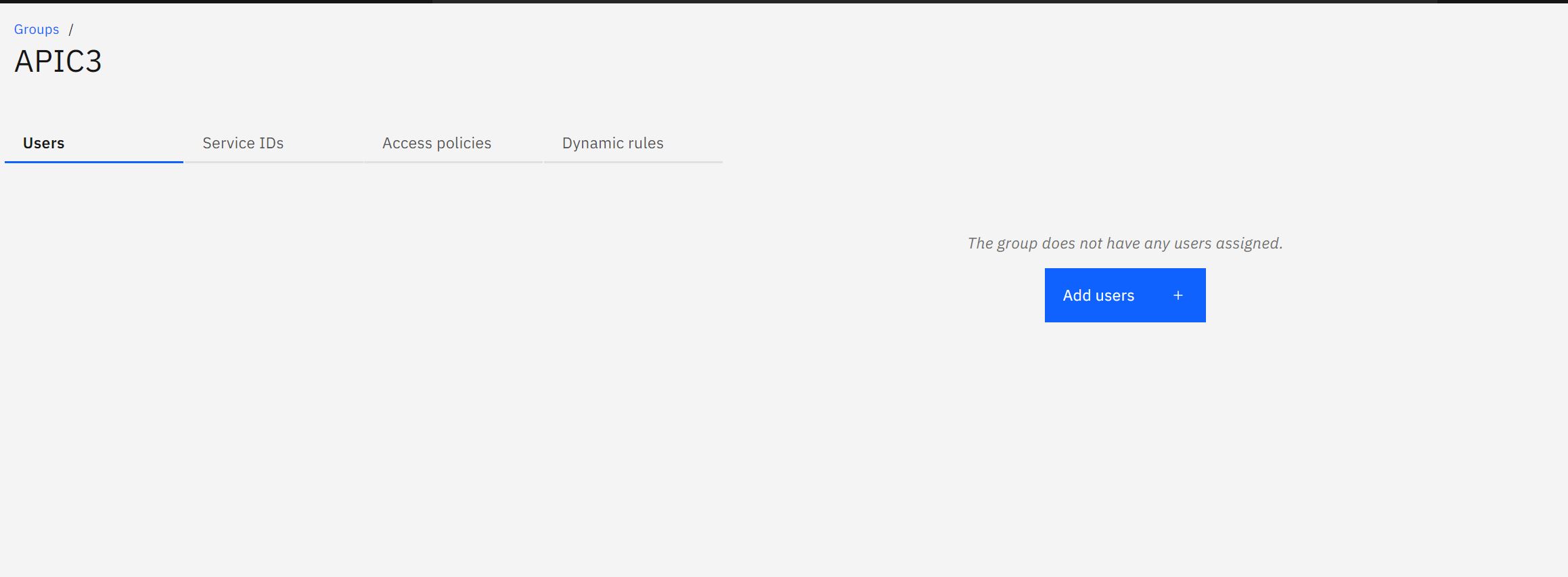
Create an Access Group
To create a group, login into https://cloud.ibm.com/iam/groups
Click on create
- Enter a name and Description and press create
- Click on Add Users to add users to the group
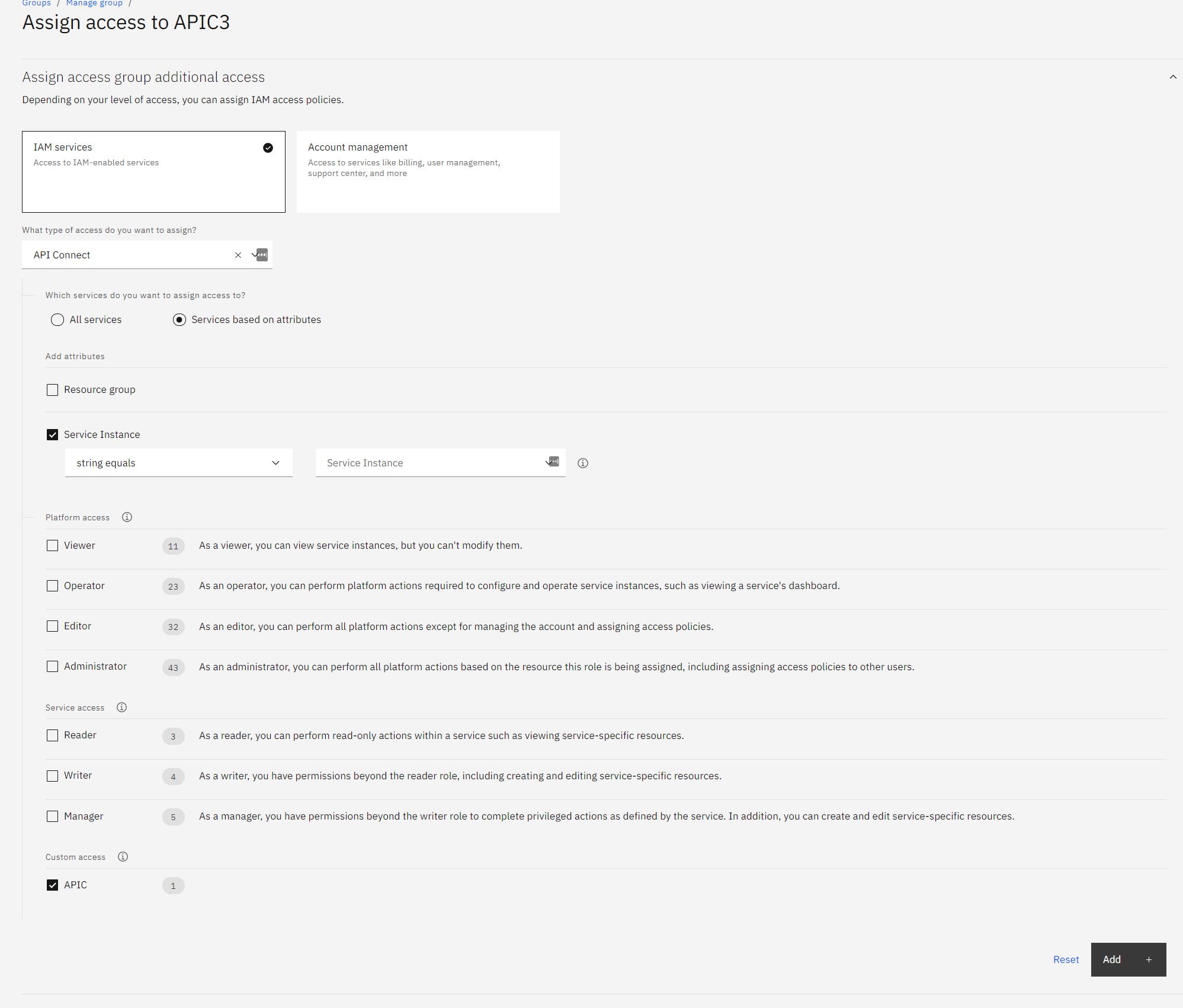
Bind a role an Access Group for specific API Connect Provide Org
To create a group, login into https://cloud.ibm.com/iam/groups
- Click on the group you want to associate with a role
- Click on
Access policies - Click on
Assign access
The roles you have created will appear under Custom access at the bottom of the list
To select which Provider Org to apply this to, click on Service based on attributes and click on Service Instance then from the drop down select the Provider Org you want this to be applied to.
Click on Add